Counter Ransomware Attacks with Cohesity
Data is crucial in the digital age, making it highly valuable and a prime target for cyber threats. Cybersecurity Ventures predicts global cybercrime costs could reach a staggering $10.5 trillion annually by 2025, with a business falling victim to a ransomware attack every 2 seconds by 2031. Despite growing awareness of digital extortion tactics, attackers are becoming more sophisticated and are explicitly targeting backup data and infrastructure, posing a continuous threat to enterprises worldwide. When businesses are compromised, it leads to significant financial losses, erodes customer trust, and in sectors like healthcare, it even jeopardizes human lives.
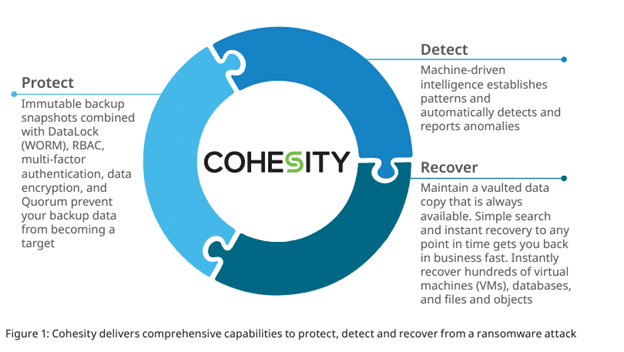
1. Protect
Advanced ransomware like Locky and Crypto now targets enterprise backup infrastructure, attempting to destroy shadow data copies and restore point data. Surprisingly, your backup, which should enhance your organization’s defense, is becoming a prime target for cyber-criminals.
Cohesity safeguards your backups, preventing them from becoming vulnerable to attacks. Using Cohesity SpanFS™, an innovative third-generation distributed filesystem, we offer strong protection against ransomware attacks with multiple layers of security. Our approach, anchored in immutability, notably provides the highest defense against ransomware assaults.
- Immutable Snapshots: In Cohesity, all backup snapshots are automatically kept in a secure, unchangeable state. The initial snapshot, the gold copy, is never accessed or exposed to any outside system or application. If you need to add new data or recover from the backup, the system automatically makes a no-cost clone of the original backup, allowing for safe changes or recovery.
- DataLock: A feature that ensures backups remain unalterable, known as WORM (Write Once Read Many). It allows designated roles like security officers to apply this setting to specific backup snapshots. Once stored in this format, the snapshots cannot be deleted, adding a solid layer of protection against ransomware attacks.
- Role-Based Access Control (RBAC): Cohesity allows your IT staff to assign specific access levels to individuals based on their roles, minimizing the risk of unauthorized access to data and systems. Each person gets access only to what they need for their specific job.
- Multi-Factor Authentication (MFA): Even if someone gains access to your system password, they can’t access Cohesity backup without passing an extra layer of security—MFA or multi-step verification. Cohesity offers a range of robust security features, including seamless integration with Active Directory, MFA, access control lists, a blend of role-based access (RBAC), and thorough auditing at both system and product levels to ensure security.
- Data Encryption: Cohesity ensures your data’s security with strong encryption. We use FIPS-validated, AES-256 standard encryption for data in transit and at rest. This encryption method has been rigorously evaluated and trusted globally, meeting the Federal Information Processing Standards (FIPS) 140-2 Level 1 standard by the United States National Institute of Standards and Technology (NIST).
- Quorum: For added security against internal threats and unauthorized changes, Cohesity mandates that any significant system alteration or root-level access requires approval from more than one authorized person within your organization.
Cohesity Helios, an advanced data management platform, offers a unique blend of features like unchangeable backup snapshots, DataLock, RBAC, MFA, and Quorum (the ‘four-eye rule’). These features work together to ensure that backup data remains protected and untouched during ransomware attacks.
2. Detect
Cohesity simplifies intrusion detection as cyber threats evolve with a global, cloud-based management solution. Using Cohesity, organizations have a unified dashboard to oversee and respond to their worldwide data and applications swiftly. To combat ransomware, Cohesity Helios employs machine learning (ML) to detect anomalies automatically and provide insights that human monitoring might overlook, ensuring enhanced security.
Our advanced machine learning algorithms constantly evaluate and automate your IT resources based on your organization’s needs. If there’s an abnormal change in your data, like an unusual data ingest rate or alterations in stored data, Cohesity Helios’ machine-powered anomaly detection notifies your IT team instantly. Instant anomaly alerting ensures quick awareness of any deviations from regular data patterns.
Cohesity’s Helios uses machine learning to establish patterns and automatically checks for unusual data changes. If it detects anything suspicious, it raises a flag, signaling a possible ransomware threat. It promptly notifies your IT and Cohesity’s support teams for quick action. Cohesity’s unique approach monitors changes in backup data and identifies unusual file activities within unstructured files and objects. Creating a baseline involves intelligently analyzing factors like file access frequency, modifications, additions, and deletions by users or applications, enabling rapid detection of ransomware attacks.
3. Recover
Cyber threats, both from inside and outside sources, can strike quickly. That’s why recovering swiftly and predictably is essential. Cohesity ensures a rapid recovery of your enterprise data and applications on a large scale. Along with unchangeable backups, Cohesity provides various policy-driven approaches to safeguard your vital data with the last secure copy. For tailored recovery and security needs, you can isolate your data in Cohesity’s cloud vault (FortKnox), replicate it to another secure cluster, or archive it to offsite storage like Iron Mountain.
Cohesity Helios speeds up recovery by suggesting a safe data copy for restoration. You can also use the platform’s powerful search to swiftly find and access data across different setups. Cohesity’s CyberScan offers a thorough view of snapshot health and recoverability status to ensure a secure restoration and prevent the reintroducing of cyber threats or software issues. It presents a vulnerability index for each snapshot and actionable suggestions to tackle software weaknesses. Helios’s continuous analysis guarantees a smooth and reliable recovery from a ransomware attack.
You can significantly minimize downtime using Cohesity’s advanced SnapTree B+Tree structure, fully loaded snapshots, and quick access through MegaFile and instant mount. You can instantly restore hundreds of virtual machines (VMs), files, objects, and large databases.
Counter Ransomware Attacks with Cohesity
Data backup serves as your ultimate shield against severe ransomware threats. Cohesity’s all-encompassing anti-ransomware solution protects, detects, and swiftly recovers vital data. This proactive approach minimizes downtime and ensures seamless business operations.

